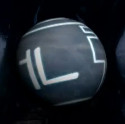Halo 4 Forerunner Sequences
< Back to Halo 4 bits / SecOp Dialogue
Forerunner Sequences

|
|
Contents |
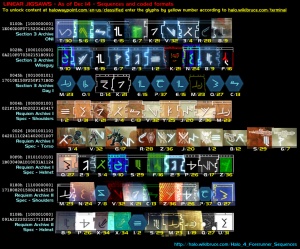
Based on the Forerunner character set used on Halo Waypoint, characters have been discovered embedded in various media releases, as well as in-game content.
Each "Linear Jigsaw" (LJ) sequence label is defined by 9 'bits', allowing glyphs number and location and full sequences to be expressed as a series of numbers, specifically as hex strings
- Current LJ sequences, puzzle pieces connected where known (*=confirmed labels)
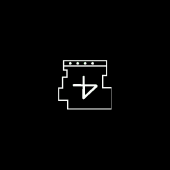
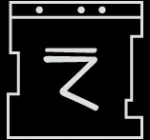
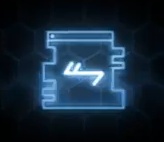
0x0004*[000000100] = 1-U-K-3-C-V-Y-J-Z-M = 0x021F15040D2023142417 (Spec - Shoulders) 0x0026*[000100110] = 3-V-G-R-Z-J-I-B-S-6 = 0x0420111C2414020C1D07 (Spec - Torso) 0x00F0*[010101010] = Q-2-3-9-S-F-2-P-G-Z = 0x1B03040A1D10031A1124 (Spec - Helmet) 0x0028*[000101000] = 9-W-E-6-2-1-K-N-8-F = 0x0A210F07030215180910 (Wiseguy) 0x0045*[001000101] = M-0-D-K-E-?-E-M-Q-C = 0x17010E150F250F171B0D (Day 1) 0x0100*[100000000] = T-5-C-E-6-K-V-3-R-8 = 0x1E060D0F071520041C09 (ONI) 0x0180*[110000000] = M-N-7-V-K-C-Z-P-?-Q = 0x17180820150D241A251B (unknown)
- Code unlocking guides on the Classified terminal displayed visually below (via HaloWaypoint.com/en-us/Classified or via HaloWaypoint on Xbox Live)
- Glyph number / transcription key
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 0 1 2 3 4 5 6 7 8 9 A B C D E F G H I J K L M N O P Q R S T U V W X Y Z ? 01 02 03 04 05 06 07 08 09 0A 0B 0C 0D 0E 0F 10 11 12 13 14 15 16 17 18 19 1A 1B 1C 1D 1E 1F 20 21 22 23 24 25
- Much of the puzzle reveals were posted by entities, AIs named Sec3OP36516, Sec3OP4243, and HydrAi on the HaloWaypoint.com forum and IRC chat. See Halo 4 SecOp Dialogue
Linear Jigsaw
Sequence 0x0004
Dot Code: 000000100
- Posted as a HaloWaypoint article, tagged classified
Sequence 0x00F0
Dot Code: 010101010
Nov 2 Bulletin - Q
- Bulletin
- Location the "Section 3" portion of the bulletin. At the end of the second CLASSIFIED line, there is a clickable link in the dot.
Last night I dreamt about physics, waldo and ancient melodies.
/START FILE/
//CLASSIFIED/
//ATTENTION ALL OPERATIVES: HIGH PRIORITY INTEL RECEIVED, REVIEW IS MANDATORY/
//CLASSIFIED/ .
/END FILE/
- The link forwards to this page with the text:
/START FILE/
//CLASSIFIED/
//ALERT: RETURN FROM BASE-LXIV IMMEDIATELY!/
//
//
//ADDITIONAL DATA RECOVERED:
/END FILE/
? - 2
? - 3
? - 9
? - S
? - F
October 29 Tweet - 2
I stood still, perched high above and looked backwards. I was caught between a hard place and a rock. http://tinyurl.com/8q5ftk6
- The tweet links to an MP4 file. The file contains meta data that reads:
- Movie Name: RECOVERED FRAGMENT
- Album: CLASSIFIED
- Recorded date: 2557
- Comment: /START FILE//CLASSIFIED//ONI HAS RECEIVED-REDACTED-/END FILE/
- Solution[1]:
- The tweet hints at between "hard place" and "rock". This says two things: Look for the HARD PLACE and ROCK plain text markers in the MP4, and then reverse the data found between
- The resulting binary file in another PNG image
- The PNG is encoded with an alpha channel, and the lower 269 scanlines contain an additional stream of bytes.
- Extract the data, making sure your method begins at the last pixel, traveling left and up, then re-save the data (344320 bytes) as an MP4 file.
-
- Inside this file is more meta data that reads:
- Movie Name: RECOVERED FRAGMENT
- Album: REQUIEM ARCHIVE I
- Recorded date: 2557
- Comment: /START FILE//CLASSIFIED//ONI HAS RECEIVED UNCONFIRMED REPORTS FROM FIELD OPERATIVES, REGARDING PREVIOUSLY UNKNOWN EMBLEM PATTERNS WHICH MAY BE APPLIED TO SPARTAN-IV ARMOR. THE EXACT MECHANISM IS UNCLEAR, HOWEVER IT MAY BE RELATED TO THE...
- One frame of this file contains the next glyph:
Oct 25 Bulletin - P
- Bulletin
- Instructions:
- View the page source to locate a link to a hidden BMP file
- Save the BMP but with a PNG extension (it's a PNG file)
- Split the image into its RGB planes
- Extract the greyscale 0-255 pixel values for each pixel and save as raw files. There are many ways this can be done. The resulting binary files are additional PNG images, as below
-
- One exception: The blue plane PNG has extra text content embedded in its binary (making it an invalid PNG as is). With the data extracted, boost the brightness to see the hidden symbol. Extracted from the file is the following text:
/START FILE//CLASSIFIED//RAIDER/EARLY REPORTS FROM IMBRIUM MACHINE COMPLEX FACILITY ARE POSITIVE - TESTING IS STILL UNDERWAY BUT SO FAR THE TEST SUBJECTS EXHIBIT THE DESIRED EFFECTS FROM THE UPDATED FERAL DESIGN./END FILE/
- Red plane text:
/START FILE/
/DATA DECRYPTION INTEL//GLYPHS
INTELLIGENCE OPERATIVES BE ADVISED: SECTION 3 HAS REPORTED A RECENT INCREASE IN GLYPH-ENCRYPTED DATA TRAFFIC.
GLYPHS CAN BE COMBINED TO FORM CODES, WHICH CAN BE USED TO UNLOCK CLASSIFIED DATA, VIA AUTHORIZED WAYPOINT TERMINALS.
CODES ARE TIED TO SPECIFIC PREREQUISITES WHICH MUST BE MET BY THE OPERATIVE PRIOR TO UNLOCKING THE DATA. PREREQUISITES APPEAR TO BE ASSOCIATED TO THE COMPLETION OF SPECIFIC UNSC MISSION OBJECTIVES. MORE RESEARCH IS NEEDED IN THIS AREA.
SEQUENCING OF THE GLYPHS INTO CODES IS NOW DETERMINED BY INTERLOCKED CONTAINERS (IT WAS PREVIOUSLY DETERMINED VIA GLYPH SEMANTICS, FOR THE ALPHA HALO ARCHIVE CODES).
/END FILE/
? - G
? - Z
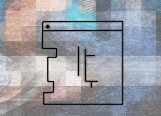
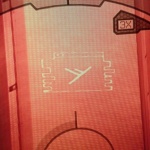
Sequence 0x0028
Dot Code: 000101000
|
| Glyphs #33, 7, 3, 2, 9 Hex: 21, 07, 03,02, 09 Alpha: W, 6, 2, 1, 8 |
Halo 4 Terminal - W 6 2 1 8
- At the end of the last terminal, "Cryptum", five new symbols are shown
? - 9
? - E
? - K
? - N
? - F
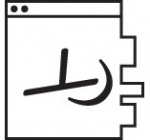
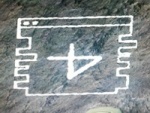
Sequence 0x0045
Dot Code: 001000101 (full code provided via HydrAi)
HydrAi via HaloWaypoint - M
- Revealed as "00-45-01-17"
HydrAi - 0
IRC - D
- In IRC, Sec0P36516 posted a hex code follow by "UP FROM Pb"
- Pb is Lead, element 82. Subtract 82 from each hex produces base64, which becomes a skydrive url
- Download SLEUTH.HYD to reveal base64
- Base64 becomes hex, decodes to base64, decodes to...
- ...resulting in the "D" puzzle piece PNG
? - K
HydrAi - E
HydrAi - A/E
HydrAi - E
Forum post - M
- Sec3OP36516 posted the piece as ascii art here
HydrAi - Q
HydrAi - C
Sequence 0x0100
Dot Code: 100000000
Xbox Live Dashboard - T
- Captured from an XBL dashboard in Australia
Oct 22 Newsletter - 5
- Newsletter - Evil Awakens
- Instructions:
- Save the JPG linked by the icon in the footer.
- Extract all binary data between "SEC3OP36516" text markers and save as a WAV file.
- Load the WAV in a program that display spectrograms (eg Sonic Visualiser), the result is the image below:
-
Oct 14 Vidoc, Making Halo 4: Infinity Multiplayer - C
datanode file - E
- Retrieve the datanode file with encrypted bytes.
- Post from Sec30P36516 contains:
76\60\10 no
luap:A8CAFBATAkEAGBAIAQEAOBQRA8CAKAQDA8CAvAgCA0AAvAwLAoAANAgCA0AAsBQbAQHAoBgLAUGAsBQdAMHAwBQYAMGAlBQbAkGA0BQLAkDAzAwNAcGA5BwdAEHA3AQOAYGAhBwMAcGA3AgNAIHA3BQcAkGAnBANAsGAqBQMA8CAlBAbAUHAzBAcAEGAjBQZA0GApBAdAADAwAAMAADAvAAZAUGApBgZAkGAzBwcAEGAsBwYA8CAzBQZAcGAhBQbAkGAvAwcAQHAlBwcAMHAhBwLAQHAuBQaA8GAwBQeAEGA3BwLAQHAuBQZAQHAuBwbAMGAvAQbA8GAjBgLAQHAuBQaA8GAwBQeAEGA3BwbAwGAhBAaA4CAkBQYA8GAsBgbAcHAvBAZAoAANAgCA0AA6AgTA8EAJBAVAEEADBwTAwEAgAAVA4EAFBgUAIFAVBwQAACAFBARA8EAOBQQAQFABBARA8CAvAgCA0AAvAwLAoAANAwLAUEAEBwTA4EABBAVAEEAEBAIAICAFBATAUFATBAUAEEADBAIAUEANBQSAQFAiAAIAUEAIBAVAACAFBATAIEANBQQAIFADBwUA4EAVBAIA8EAUBAIAQFASBwTAYEAGBQRAACAHBgTAkEAPBwRA4EAPBAIAUEAIBAVAACAOBQSAACAFBwRAEEAHBgTAUEAgAQWAwEAFBAVAEEAJBARAUEANBQTAkEAgAAVAMFAVBQTAACAMBQRA4EAOBwTAMFASBQRAAFAgAATAwEABBAIAECAUBgUAUEAMBQQA8CAvAgCA0AAvAwLAoAANAwLAQEAFBQSAYEAJBwUAMFABBATAMEAvAwLAoAANAwLAUEAMBQSAYEAgAAVAIFABBAVAMFAvAAACIZY0FGZAABAEAgAxCBAAwKRAIAABAAAAABI01mZFZVQXBAACYrRGlkU - Reverse bytes = base64 => WAV file
- Extract data segment of the WAV file (remove header and every other/null byte), reveals text:
/START FILE/
//CLASSIFIED/
//
//ALERT! ALL PERSONNEL MUST IMMEDIATELY ENGAGE IN THE ONGOING EFFORT TO UNSCRAMBLE THE "TIME CAPSULE" DATANODE/
//
//DATANODE CURRENT LOCATION:
download.halowaypoint.com/content/waypoint/assets/images/classified/0000timecapsule/1jk4giqwr67g3af97qwyg739-timecapsule.html
//
//
/END FILE/ - The linked "timecapsule" page contains:
/START FILE/
//CLASSIFIED/
//
//RECOVERED DATA NODE (HEAVILY ENCRYPTED):
// //
//
//
//
//(REQUIRES KEY FOR DECRYPTION)/ /END FILE/ - The Lock image links to the raw datanode file
- Post from Sec30P36516 contains:
- Determine the key required to decrypt the datanode
- A post by Sec0OP36516 contains:
/STRT FL/////CLSSFD/////N STNDRD NCRYPTN PRTCLS ND PTTRNS////mblms r Ky. r y lkng fr ky? Fnd yr ky blw...//////ND FL/
AS;LKFJLQ4NRAJL;ASJZPOIJ4PJUNK89UF9832JRTLKMNFA./SD,MVCKFJG
NYT4RH7ARFLSZIMTN3...........4UI0YR86DFVFTYUHJUNKXIOCUVYSHWE4RKJLNMLK
VJZDXI7VYHA;FLIJ89DUFJSREGJDO...Z8VUJZDLIJFSDIFUA08DYUV7AWEHJF;LISJADVLKJZXDV89
0JLIFJ;EWLJMFASD0F98JSDIOVJMDKLDJGF[QOUJ-A8UJV.JFAJF34PJNS9ZDVHJ34JFS0V98J2JENAJVPAJI......ASFAFWEFHGT3GWGBSDVDSVAAFAA.....
......................................................................
.............................................................................. - The period after "A8UJV" is a link to the 'intrigue' page
- The linked page contains:
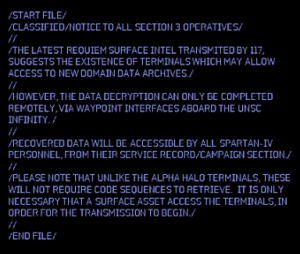
/START FILE/
//CLASSIFIED/
//
//WORK IN PROGRESS:
//
//
//
//
/END FILE/ - The download image links to an MP4 file. Meta headers contain: Title: "RECOVERED FRAGMENT", Artist: "ONI/SECTION3", Description: "ONI DECRYPTION KEY FORMAT: ../5124587109-reach-mia-key-format"
- a) One frame of the MP4 contains instructions:
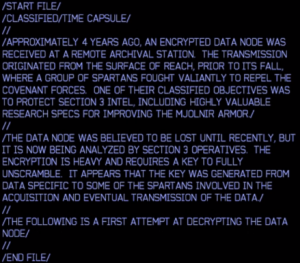
- b) Following the meta Description, link to a url which displays:
0000-????-???W-????-?-???Z-???-????-????-???-?0?8-??7-???8-W???-?47-??W-?00?-?0?-????-W???-????-?Y??-????-??Y-Y???-????-???-?0?-???Y-???-????-???-??W-?6??-????-???-W???-???-????-W??-??Z4-?0?-???W-????-???-????-????-??7-???0-??Z?-????-??0?
- A post by Sec0OP36516 contains:
- Determine the contents for the key to decrypt the datanode
- A post by Sec30p36516 contains:
/START FILE/
//CLASSIFIED/
covenant::(base64)
john::(base64)
librarian::(base64)
marscolony::(base64)
mendicant::(base64)
napoleon::(base64)
nasa::(base64)
precursor::(base64)
shaw::(base64)
unsc::(base64)
/END FILE/ - Note prefix text, and place rows in chronological order:
Precursor, Librarian, Mendicant, Covenant, Napolean, Nasa, Marscolony(2080), UNSC(2160-2164), Shaw(2220-2317), John(2511-?) - Base64 strings => raw data, combined in order => PNG
- Text link to frame piece for piece 00F0-Z
- Embedded in the PNG is data between "SEC3OP36516" strings. Extracted leaves:
/garbage/a few more than five dozen russian dolls/garbage/(base64) - base64 => WAV
- Extract data segment of the WAV file (remove header and every other/null byte) for another WAV file
- a) Spectrogram reveals glyph for piece 00F0-Z
- b) WAV meta headers include Director: "ONI/SECTION3", Date: "2557", Comment: "../00002552-reach-mia-64hz.lo"
- Download the .lo file and rename to WAV
- Extract data segment of the WAV file (remove header and every other/null byte) for base64 data
- base64 => MP4 video
Meta headers include: Name: "RECOVERED FRAGMENT", Album: "???", Date: "2557", Description: "/START FILE/CLASSIFIED/RECOVERED EMBLEMS FROM A FEW IDENTIFIED ONI COLLABORATORS/END FILE/" - Locate and identify the callsign for each Halo: Reach user's emblem.
- A post by Sec30p36516 contains:
- Resulting key: 0000-VGNS-CLAW-BEES-K-RADZ-KON-CULT-A3LG-TOA-S038-S27-D118-WULF-O47-DEW-J009-S01-BNDR-WOLF-EIRE-RYAN-PNDA-SKY-YMCA-GL13-MOA-F09-KRPY-3UP-MG91-MAK-LAW-S692-TEXX-BOB-WURF-AIR-JEDI-WPX-RAZ4-M0A-SOCW-XENO-GUS-SSDD-ES91-117-U190-ENZO-IIII-RC0N
- Apply the recipe algorithm
- Resulting MP4 video:
- a) Meta tag text includes "ONI/SECTION3", "FILE/CLASSIFIED/CODE RECOVERY NEARING COMPLETION FOR JVC3 - 2 AND REQ I-3/END"
- b) Two glyphs on the spinning ball are "E", and sequence 00F0-2
- c) Also hidden as a spectrogram in the audio is piece 00F0-9
Oct 29 Trailer - 6
- Spartan Ops Trailer 1
- p1) At the end of the trailer is a single frame with the ONI symbol, and when viewed and enhanced contains a faint outline of a puzzle piece.
- p2) Near the end of the trailer at the title sequence, there's a quiet audio squeal[2]. This is another spectrogram, which when analyzed produces the following symbol, combined below with the puzzle frame:
Oct 17 Bulletin - K
Nov 2 Bulletin - V
- (continuing from above) The "oni.gly" reference becomes another URL:
- When viewed with a hex editor, the file appears to be a WAV formatted file. Interleaved with the WAV data, however, are null (00) value bytes. Removing the WAV syntax segments and these null bytes produces a hidden GIF file, which contains the glyph for "V":
Oct 16 Newsletter - 3
Xbox Live Halo 4 Marketplace - R
- Located in the Halo 4 product page of Xbox Live between loading screens[3]
Oct 18 Facebook Image - 8
Sequence 0x0180
Dot Code: 110000000
Spartan Ops - M
- The glyph can for "N" can be found in the Spartan Ops level Spartan Mountain.
- Piece image was also linked directly in IRC chat
Spartan Ops - N
- The glyph for "N" can be found in the Spartan Ops level Sniper Ally.
Brute Forced - 7
Halo 4 Guidebook - V
- The glyph for "V" is located in the guidebook[4]
Spartan Ops - K
- The glyph for "K" can be found in the Spartan Ops level Secred.[5]
Nov 2 Bulletin - C
- (continuing from above) Secondly, there is an image linked in the source call "empty.png". Open the file and adjust the brightness to reveal the text:
- ..\images\mc?-???-???-???-???-???-???-???\classified.mp4
- Additionally, the above web page source includes a very large collection of comments, implying it should be ignored. But in the center of this suspicious pattern is a base-64 string:
- TVRoZAAAAAYAAAABA8BNVHJrAAAAbQD/IAEAAP8DFS8vQ0xBU1NJRklFRC8vRT1tYzMvLwDAWwCQNECWQIA0AACQNkCHQIA2AACQN0CHQIA3AACQNkCHQIA2AACQOUCHQIA5A
ACQN0CHQIA3AACQNkCWQIA2AACQNECeAIA0AAD/LwA=
- TVRoZAAAAAYAAAABA8BNVHJrAAAAbQD/IAEAAP8DFS8vQ0xBU1NJRklFRC8vRT1tYzMvLwDAWwCQNECWQIA0AACQNkCHQIA2AACQN0CHQIA3AACQNkCHQIA2AACQOUCHQIA5A
- Converted to a binary string, the base-64 becomes a MIDI file, playing the classic Halo monk theme. Embedded inside the binary, however, is the phrase:
- //CLASSIFIED//E=mc3//
- Following the note progression in the tune, applied to the mc??? path, a new URL and MP4 file is discovered:
- Extracting the audio stream and performing another spectrogram produces two images, one of which is a Forerunner glyph:
- Additionally, one frame in the classified.mp4 includes additional information:
Spartan Ops - Z
- The glyph for "Z" can be found in the Spartan Ops level Core.[6]
Spartan Ops - P
- The glyph for "P" can be found in the Spartan Ops level Clean Up.[7]
Brute Forced - A/E
Spartan Ops - Q
- The glyph for "Q" can be found in the Spartan Ops level The Challenge.
Reference puzzles
Recipe
- From forum post containing:
/START FILE//CLASSIFIED/ONI FIELD MANUAL EXCERPT/ON ASSIGNMENT, IT IS OFTEN NECESSARY TO IMPROVISE IN ORDER TO STAY HEALTHY AND WELL FED. ONI DOES NOT EXPECT ALL PERSONNEL TO BE CULINARY EXPERTS, BUT YOU MUST UNDERSTAND BASIC PRINCIPLES AND RECIPES. RECIPES ARE CRUCIAL, AS THEY ALLOW YOU TO CONVERT TWO SEEMINGLY DISPARATE INGREDIENTS, INTO A WONDERFUL DISCOVERY OF FLAVOR./
/END FILE/
//START FILE//CLASSIFIED/MISSING DATA RECOVERED FROM THE SPARTAN NV66:
[ascii] (with period appended to one line)
/END FILE/ - The period is a link to a CSV file
- The raw data is combined CMYK pixel planes. Recombine the planes to create a 925x491 CMYK image.
- Image describes the "recipe":

Note: A secondary puzzle revealed an "official" source algorithm:
- From forum post containing:
/START FILE//CLASSIFIED//INTERCEPTED COMM/COME DOWN FROM Uus, IT'S TOASTY DOWN HERE/END FILE/
(long string of hex) - Hex => base64 => Hex
- "Uus" refers to element Ununseptium, element 117. "Come down from Uus" = subtract 117 from each Hex value
- Hex-117 => base64 => recipe source code
Recipe algorithm can be represented as follows:
int size = datanode.Length / 2;
byte[] output = new byte[size];
int index = 0;
for (int i = 0; i < size; i++)
{
int a = ((key[index] % 2) == 0 )? 0 : 1;
int b = ((datanode[(i*2)+1] % 2) == 0)?0:1;
int val1 = datanode[(i * 2)] + a;
int val2 = val1 * 2;
int val3 = val2 - b;
int val4 = key[index];
int val5 = val3 - val4;
output[i] = Convert.ToByte(val5);
index++;
if (index >= key.Length)
{
index = 0;
}
}